

Network Penetration Testing Fundamentals
In the ever-evolving cyberspace when the hackers are extensively going after any organization irrespective of its size, it is important for an organization to ensure that it puts into best efforts to ensure the security of its technical infrastructure. Penetration testing rightly helps an organization by finding and identifying vulnerabilities, assessing the damage, and mitigating them before they are found and exploited by an attacker or a group of attackers. Types of penetration testing include network penetration testing, web application penetration testing, mobile application penetration testing, cloud penetration testing, IoT penetration testing, etc.
Why is a Vulnerability Assessment not sufficient?
When it comes to an organization’s security, a vulnerability assessment alone is not sufficient. Penetration testing activities dug deeper into the organization’s technical infrastructure. Generally, a vulnerability scan is performed using an automated scanner with a set of pre-defined vulnerabilities. Here, we can interpret that these scanners are not context-aware, and hence, they are not capable of comprehensively understanding essential security controls and critical business functions.
Network Penetration Testing
While conducting a network penetration testing activity, the primary goal of the network penetration testers is to identify vulnerabilities which can be exploited by the attackers in an organization’s network devices such as routers, switches, systems, hosts, etc. If a vulnerability exists in any of the network-connected assets of an organization, the hackers might be able to compromise them and use in such a way which allows unauthorized access to its sensitive data, remote access, etc.
Apart from running automated tests, the importance of manual tests cannot be denied as the testers are context-aware, and they are familiar with the critical business functions of an organization. At Breachlock, we believe in adopting an attacker-like mindset and simulate real-life attacks on an organization by using controlled exploits. Our methodology includes steps such as –
- Information Gathering: In this phase, a comprehensive scan or survey of your organization’s network is carried out. Just like a geographical map, all the devices connected to your organization are mapped so that the entire network is visualized easily.
- Scanning: Here in this phase, the network penetration testing process continues with performing port scans to find closed, filtered, and open ports on the devices connected to a network.
- Fingerprinting: After initial scans are completed, OS fingerprinting is carried out in network penetration testing for finding OS type, version, patch level, type of system, and running protocols. In small organizations, the second and third phase are often combined together into a single phase.
- Vulnerability Scanning: After fingerprinting is concluded, the testing team performs a vulnerability scan, which can be either automated or manual. In cases of automated scans, they are matched against a common vulnerability database like CVE to verify the existence of vulnerability as well as any publicly available exploit.
- Report: Being the conclusive phase of a network penetration testing exercise, detailed reports are created and presented to the client containing information such as executive summary, findings, and suggestions, recommendations, etc.
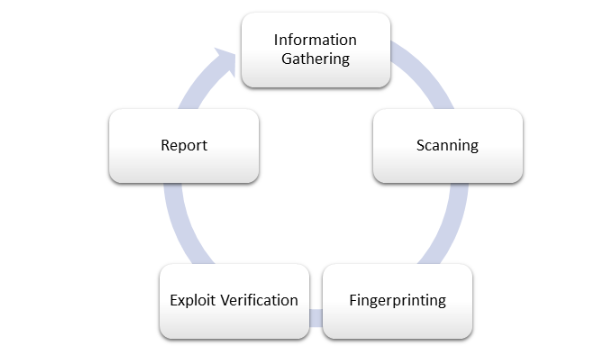
Figure 1: Network Penetration Testing Steps
Some of the frequently asked questions to us about network penetration tests are –
- Why should my organization conduct a network penetration test?
A network penetration testing activity helps your organization, or the decision-makers or the internal security team in gaining valuable, useful, and actionable insights into the existing security posture of the network assets that were under the scope. Accordingly, if any vulnerability, loophole, flaw, or weakness is found, it can be addressed before it is exploited by the attackers. - How much time does it take to conduct a network penetration test?
The time taken for a network penetration test to be completed varies from one organization to another depending upon the complexity and size of networks. On average, our team finishes a network penetration testing project between one week to four weeks. - What is the difference between a penetration test and a vulnerability assessment?
Check this post here. - What is the cost of a network penetration test?
This is the most difficult questions, and it is not at all easy to be answered by you experts unless they are somewhat familiar with your network. However, as a matter of general practice, network complexity and number of components are deciding factors in determining the cost. Do get in touch with us to discuss further.
If you are interested in improving your network security,conduct effective network penetration tests and identify vulnerabilities in your system. Don’t wait until it’s too late – schedule a call today and protect your business from cyber threats!







