BreachLock provides a wide array of professional services to enhance the effectiveness of your customer experience and help you reach your security goals. Please check out our packages to see how we can best serve your needs.
Dynamic Application Security Testing (DAST)
BreachLock DAST is a black box pentesting method with a running instance of an application. It examines examining it from the outside in, its running states, and observes its responses to AppSec penetration testing. To identify vulnerabilities, various inputs are sent, and responses are analyzed typically later in the software development lifecycle, after an application is deployed and running in a production environment.
Cloud Pentesting
BreachLock cloud pentesting focuses on evaluating the security controls, configurations, and access mechanisms within hybrid and multi-cloud infrastructures, public clouds such as AWS, Azure, GCP, as well as Containers, Kubernetes, and the Control Plane. As organizations increasingly migrate their infrastructure and services to the cloud, pentesting helps you understand the security risks and vulnerabilities specific to cloud-based resources.
DevOps Pentesting
Support your Secure Development Lifecycle (SDL) by ensuring that the software you develop is inherently secure and resilient to cyber threats by fostering automated collaboration between your development and operations teams through DevOps penetration testing conducted for SDL, SCR, and DAST.
Standardized Built-in Framework
The BreachLock Platform is a standardized built-in framework that enables consistent and regular benchmarks of attack tactics, techniques, and procedures (TTPs), security controls, and processes.
BreachLock Technology
The BreachLock Platform and can analyze vast amounts of data in real-time to identify complex patterns and anomalies faster and more effectively, predicting an exploit before it happens.
Enhance Accuracy
By automating routine security tasks and the decision-making process, our NLP-based AI models can reduce the likelihood of human error of your continuous security testing process.
Accelerate Speed and Effectiveness
Multiply not only scale, but the speed of vulnerability identification and prioritization. Based on the interpretation of large data sets, historical data, and thousands of evidence-based tests, we uncover patterns impossible to detect solely with manual methods.
Achieve Greater Scalability
Our Platform can handle large-scale data analyses and security tasks for large enterprises. Based on thousands of POC samples from testing, true or false positives are categorized in real-time, enabling greater scalability to reduce your attack surface.
Enrich Contextual Insights
The BreachLock NLP-based AI models offer a more advanced and nuanced approach for providing deeper and more enriched contextual insights around the most exploitable points of interest by an attacker.
Maximize Flexibility & Versatility
BreachLock Cyber Security Validation and Exposure Managment solutions align precisely with your business and security requirements, giving you the flexibility and versatility to choose the solution and methodology that works best for you.
Industry Peer Benchmarking
Gauge your security posture against industry peers. Through extensive experience and accumulated knowledge of unique attack paths and TTPs, data intelligence will help to set measurable and consistent benchmarks to improve your security posture over time.
Achieve Compliance
Meet your compliance and business requirements and adhere to industry standards like HIPAA, PCI DSS, ISO 27001, SOC 2, and GDPR and download certifications that are accepted by auditors and customers directly from our Platform.
Dedicated Project
Track Real-Time
Remediation
Unlimited
Unlimited Support &
DevOps
Comprehensive Pentesting
CREST-Certified
Private PTaaS Solution
Several large enterprises and their internal pentesting and red teams are already using BreachLock’s private PTaaS solution. Our multi-tenant technology is flexible to host dedicated instances per client. Our human-delivered and continuous pentesting workflows help clients scale their internal teams to accommodate larger workloads and faster testing.

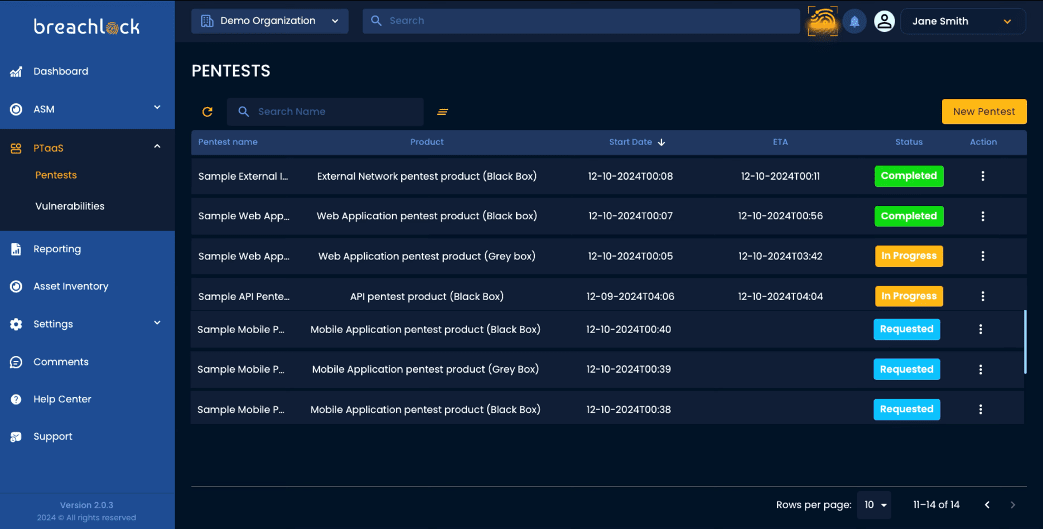
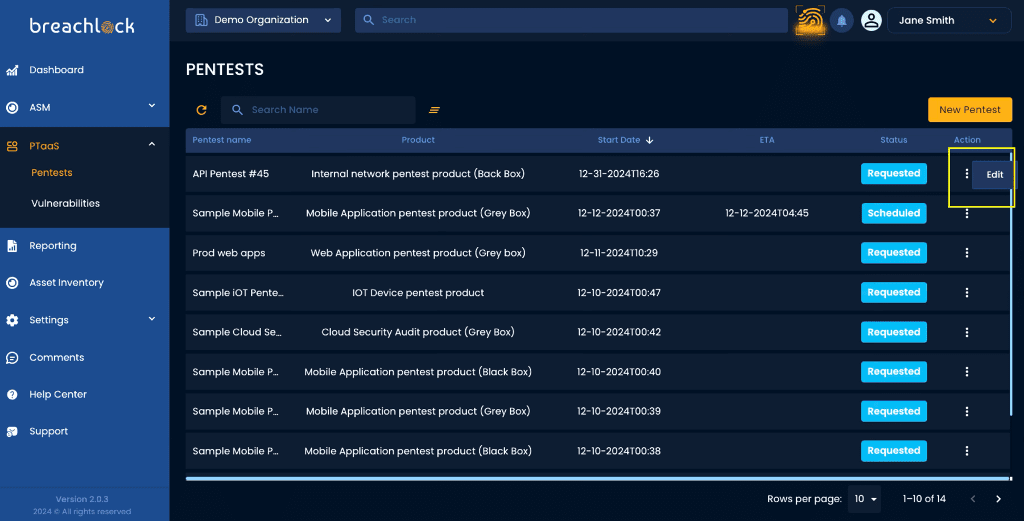
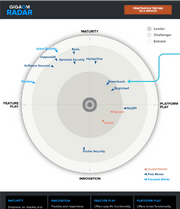
Industry recognitions we have earned